Resource / Online Journal
Comprehensive Guide to AWS IAM: Policy Management, Authentication, & Access Strategy
Optimizing AWS IAM for Security, Compliance, and Operational Excellence with External Tools Integration. Learn how integrating AWS tools with external products enhances governance, compliance, and operational needs.
Published on Feb 26, 2025

Executive Summary
AWS IAM (Identity and Access Management) is a powerful tool that allows you to manage identities, permissions, and access within Amazon Web Services (AWS). This comprehensive guide provides you with a complete understanding of AWS IAM and its critical features, including policy management, user and NHI administration, authentication, monitoring, and privileged actions. It also emphasizes how integrating AWS IAM with external tools and products can help organizations build a robust identity and access strategy.
Key recommendations for building a robust identity and access strategy include leveraging AWS native capabilities for automation and scalability, while incorporating external tools like SailPoint, Okta, CyberArk, and Prisma Cloud to enhance governance, compliance, and monitoring. This blog serves as a guide to help organizations choose the right identity and access management (IAM) solutions. It emphasizes the importance of tailored decision-making, recognizing that every organization has unique needs when it comes to balancing security, usability, and cost.
What are AWS IAM, and Why Should You Care?
Identity and Access Management (IAM) in AWS is crucial for ensuring that only authorized users, roles, and systems have access to your AWS resources. These attributes are used only if authentication is not externalized to an Identity Provider (IdP) like Okta or others. When IAM authentication is handled directly within AWS, you can use AWS Console, CLI, or API, Infrastructure-as-Code (IaC) with Terraform/ CloudFormation with built-in features for scalability, automation, and auditability.
1. AWS IAM Concepts
1.1 Understanding Account Attributes
Root Account Attribute
Account Email: The account email is the email address used to create your AWS account. It serves as the primary method for logging in as the root user and is also linked to your billing information.
Account Contact Information: Located in the Account Settings of the AWS Console, this section stores your organization’s name, address, and phone number. It’s mainly used for billing and support purposes, ensuring AWS can reach you when necessary.
Root User Credentials: Your root user credentials consist of the username (your account email) and password. These credentials provide full access to your AWS account, so it’s crucial to follow best practices: enable Multi-Factor Authentication (MFA) and avoid using root credentials for everyday tasks. By following these steps, you ensure an extra layer of protection for your account.
IAM User Attributes:
AWS IAM (Identity and Access Management) doesn’t store personal details like first name, last name, or email for each user by default. Instead, it focuses on specific attributes for each IAM user.
User Name (Username): The user name is a unique identifier you create for each user, such as "jdoe" or "service.account1". It’s used to identify each individual or service account within AWS IAM.
ARN & User ID: The ARN (Amazon Resource Name) and User ID are automatically generated by AWS. They serve as unique references for each user, ensuring there are no conflicts and enabling secure access controls within your AWS environment.
Path (Optional): The path is a customizable prefix you can assign to organize users or groups (e.g., "/dev/", "/finance/"). It helps categorize users, making it easier to manage and maintain access control.
Creation Date: The creation date is a timestamp that records when the IAM user was created. This information is useful for tracking and auditing purposes.
Optional Attributes for Internal Authentication
If you're managing user authentication directly within AWS IAM (instead of using an external identity provider like Okta), the following attributes are relevant:
Password-Related Info: If a console password is set for the user, AWS tracks when the password was last used. This helps you monitor access.
Attached Credentials: Attached credentials include any Access Keys (Key ID & Secret Key) for programmatic access, as well as MFA configuration if enabled. These credentials ensure users can securely interact with AWS resources.
Tags (Optional): Tags are customizable key-value pairs you can assign to users (e.g., FirstName=John, LastName=Doe, Email=jdoe@example.com). These tags help store additional information about users, making it easier to manage and retrieve specific details when needed.
Entitlement Types & Their Attributes
| Entitlement Type | Key Attributes | Description and Example |
| Group Membership | Group Name, Group Policies | In AWS IAM, a group is a collection of users who share the same set of policies, simplifying permission management. Example: You could create a “DBA_Backup” group that grants backup privileges for MySQL and PostgreSQL RDS databases. A policy like rds: CreateDBSnapshot could be applied, with conditions, such as restricting backups to a specific bastion host via an IP-based constraint. |
| Identity-Based Policy | Policy Document (JSON with Effect, Action, Resource, Condition), Attached To (user, group, or role) | As mentioned above, Identity-based policies are attached directly to IAM users, groups, or roles, specifying what actions are permitted or denied for each entity. Example: If a policy is attached to a user's role, that user can only perform actions defined by the policy, such as accessing a specific resource. |
| Resource-Based Policy | Resource ARN, Principal (who can act), Actions (e.g., s3:GetObject), Effect | For assignments within the same AWS account, it's recommended to use identity-based policies. These policies help manage permissions for users, groups, and roles in a centralized way, ensuring clear governance and visibility. Resource-based policies should be reserved for granting access across different AWS accounts, allowing resource owners to directly control permissions on the resource. Example: If you need machines or programs in multiple AWS accounts to access a centralized S3 bucket, a resource-based policy would grant the necessary permissions to non-human identities (NHIs) created in each account, enabling secure cross-account access. |
| Role Assignment | Role Name, Trust Policy (who can assume), Attached Policies | Roles offer temporary access without the need to create new accounts. Trust policies define which entities, such as users, services, or applications, are allowed to assume the role. Example: A script or application might assume a role to call AWS IAM APIs. Trust policies can further secure this by restricting access based on specific tags, VPCs, or IP ranges, which helps minimize potential attack surfaces in the event of a role compromise. |
| Permission Boundary | Boundary Policy (max allowed actions), Attached To (user or role) | A permission boundary is an advanced security feature that limits what a user or role can do, even if they are assigned permissions that would typically allow more actions. Example: You can define a whitelist of allowed permissions for a user or role. Even if additional permissions are mistakenly assigned later, the permission boundary ensures they cannot be used, keeping the actions within the defined limits. |
| Service Control Policy (SCP) | Policy Document (org-level restrict/allow), Scope (applies to OUs/accounts) | AWS Organizations is a service that helps centrally manage and govern multiple AWS accounts from a designated management account. It acts as a framework to organize your accounts, ensuring efficient administration, centralized billing, policy enforcement, and simplified management across your organization.
Service Control Policies (SCPs) are applied at the organization level in AWS Organizations to govern actions across multiple accounts. These policies enforce specific restrictions and guidelines across your AWS environment. Example: To ensure all resources in your AWS accounts align with your security standards, an SCP could prevent the creation of unencrypted S3 buckets. This would ensure all data stored in S3 is encrypted by default, promoting security best practices and reducing the risk of errors or non-compliance at the organization level. |
| Session Policy | The policy passed during AssumeRole restricts actions for the temporary session. | Session Policies add an extra layer of security when assuming an AWS role by limiting the permissions granted during a temporary session. These policies ensure that only the necessary actions are allowed, helping prevent excessive permissions from being granted during that time. Although it can be difficult to ensure users or applications strictly adhere to session policies—especially since they may still meet their goals without them—the key is to programmatically attach session policies when a role-based session is initiated. A practical solution is to use AWS EventBridge (formerly CloudWatch Events) to monitor AssumeRole API calls. This allows you to trigger a serverless function that can assess the characteristics of the workload assuming the role. Based on that assessment, you can dynamically apply additional restrictions, ensuring that only the necessary permissions are granted during the session. |
Recommendations
Policy Recommendations
AWS offers a range of policies to define and manage access, permissions, and governance across your environment. Here’s an overview of key policy types and best practices for managing them effectively:
Policies Included: Group Policies: Identity-Based Policies, Resource-Based Policies, Trust Policies, Permission Boundary Policies, Session Policies, Service Control Policies (SCPs).
AWS Native Tools: AWS native tools are ideal if your environment is mainly AWS-based and you need seamless integration for policy and role management.
External Products: External products offer added governance and security measures beyond AWS, making them valuable for organizations with multi-cloud environments or specific security requirements.
| AWS Tool | Description |
| AWS Console, CLI, API, or Infrastructure-as-Code (Terraform/ CloudFormation) | You can create and manage policies and entities in AWS IAM using a variety of tools that offer scalability, automation, and auditability. |
| External Products: | Description |
| IGA Tools (e.g., SailPoint, Saviynt, Okta) | These tools centralize governance for group, identity-based, and boundary policies with workflows and periodic reviews. |
| CNAPP Tools (e.g., Palo Alto Prisma Cloud, Wiz, Orca Security) | They offer resource-based policy management and enforcement for securing cloud-native workloads. |
| CSPM Tools (e.g., Check Point CloudGuard, Lacework, Rapid7 InsightCloudSec) | These tools monitor, audit, and enforce SCPs and trust policies for compliance and governance. |
| CWPP Tools (e.g., CrowdStrike Falcon, Trend Micro Cloud One, McAfee MVISION Cloud) | They manage session policies and trust policies to secure containerized workloads and infrastructure. |
Aggregation Entities Administration Recommendations
Scope: Organization, Group, Role
Options for Configuration:
| AWS Tools | Description |
| AWS Console | It directly creates and manages organizations, groups, and roles via the AWS Management Console. |
| AWS CLI | AWS CLI is used to script and programmatically create organizations, groups, and roles. |
| AWS API | Integrate AWS API calls into custom workflows or automation systems to dynamically create and manage entities. |
| Terraform or CloudFormation | Define and deploy organizations, groups, and roles as Infrastructure-as-Code (IaC). |
| External Products | Description |
| IGA Tools (e.g., SailPoint, Saviynt, Okta) | These tools enable centralized governance and workflows to create and manage groups and roles efficiently, ensuring alignment with identity governance processes. |
| CNAPP Tools (e.g., Palo Alto Prisma Cloud, Wiz, Orca Security) | Facilitate creation of roles and configurations for workloads in cloud-native environments. |
| CSPM Tools (e.g., Check Point CloudGuard, Lacework, Rapid7 InsightCloudSec) | They allow creation of organizational structures and roles as part of centralized configurations in cloud environments. |
User Administration
Scope: Creation of IAM users and assignment of entitlements such as roles, groups, and policies specifically for human users.
Options for Configuration:
| AWS Native Tools | Description |
| AWS Console, CLI, API, or Infrastructure-as-Code | Use AWS Console, CLI, API, or Infrastructure-as-Code (Terraform/CloudFormation) to create and manage organizations, groups, and roles with automation, scalability, and auditability. |
| External Products: | Description |
| IGA Tools (e.g., SailPoint, Saviynt, Okta) | Enable centralized governance and workflows to create and manage groups and roles efficiently, ensuring alignment with identity governance processes. |
| CNAPP Tools (e.g., Palo Alto Prisma Cloud, Wiz, Orca Security) | Facilitate creation of roles and configurations for workloads in cloud-native environments. |
| CSPM Tools (e.g., Check Point CloudGuard, Lacework, Rapid7 InsightCloudSec) | Allow creation of organizational structures and roles as part of centralized configurations in cloud environments. |
Privileged Account Monitoring (PAM)
Scope:
Monitor and manage Break the Glass Activities, Emergency Assignments, Privileged Session Recording, Shared Accounts Administration, and Break the Glass Account Administration.
| AWS Native Tools | Description |
| AWS Native Tools | Use AWS IAM, CloudTrail, Config, and Session Manager for basic privileged activity monitoring, limited session recording, and anomaly detection via GuardDuty and Security Hub. |
| External Products | Description |
| PAM Tools (e.g., CyberArk, BeyondTrust, Delinea) | Provide advanced features like privileged session recording, just-in-time privilege escalation, shared account governance, and break-glass account workflows. |
| IGA Tools with PAM Capabilities (e.g., SailPoint, Saviynt) | Integrate privileged account governance with workflows for emergency privilege escalation, periodic reviews, and centralized management. |
| CNAPP Tools (e.g., Palo Alto Prisma Cloud, Wiz) | Monitor cloud-native environments for privileged misconfigurations and excessive permissions but offer limited session recording. |
| CSPM Tools (e.g., Check Point CloudGuard, Lacework) | Audit and alert on privileged access risks across cloud accounts with a focus on compliance and excessive privilege detection. |
Note on Scoping AWS IAM Accounts for PAM:
When determining which AWS IAM accounts should be scoped for PAM (Privileged Access Management):
Policies and Permissions: Accounts with high-risk permissions (e.g., resource provisioning administrative tasks) require PAM, while low-risk, read-only accounts may not.
Application Classification: Compliance, risk severity, and business criticality of accessed applications guide the need for PAM.
Nature of the Account: Named, shared, break-the-glass, and NHI accounts should be evaluated based on usage and associated risks.
Frequency and Scope: Rare, high-impact activities warrant PAM, while frequent, low-risk actions may not.
This ensures PAM is applied where it adds the most value without unnecessary complexity.
Non-Human Identities (NHIs)
Scope:
Create Non-Human Identities (NHIs) and assign entitlements (roles, policies) to them, ensuring proper governance, secure storage, and lifecycle management.
| AWS Native Tools | Description |
| AWS Console, CLI, API, or Infrastructure-as-Code (Terraform/ CloudFormation) | Used to to create NHIs and assign entitlements with consistency, scalability, and auditability. |
| External Products | Description |
| NHI Governance Tools (e.g., Natoma, Veza, Astrix) | Automate NHI lifecycle management, including creation, secure credential storage, and credential rotation, while enforcing Zero Trust principles. |
| IGA Tools (e.g., SailPoint, Saviynt) | Enable governance workflows for NHI entitlements, including approval processes, periodic reviews, and compliance tracking, with integration for lifecycle management. |
A Note on Role vs. NHI
Navigating workload security and NHI presents valuable opportunities for threat modeling and creating effective best practices. When securing machine interactions in AWS IAM.
Role-Based Approach: Rather than creating an NHI (Non-Human Identity), allow the machine or program to assume an IAM role to perform the required operations.
NHI-Based Approach: Create a Non-Human Identity (NHI) and allow the consuming program to use it for performing IAM operations.
Hybrid Defense-In-Depth Approach: Implement multiple layers of defense in line with Zero Trust Architecture principles, here’s how it works:
Create the NHI and store it securely in a Secret Store.
IAM Policy: Design policies so that any program needing credentials must first assume an IAM role.
Credential Rotation: Leverage cloud provider features to automatically rotate credentials after every use. This minimizes the impact of potential credential exposure by ensuring that once used, they are rendered useless and requiring the IAM role to fetch new credentials.
Authentication
Scope:
Enable secure access using Federation, Single Sign-On (SSO), and Multi-Factor Authentication (MFA) for robust and scalable identity authentication, including password less authentication options.
| AWS Native Tools | Description |
| AWS IAM Identity Center (formerly AWS SSO) | For managing federated access, enabling SSO for AWS resources, and enforcing MFA. Configure these features using the AWS Console, CLI, API, or Infrastructure-as-Code (Terraform/CloudFormation) for automation and auditability. |
| External Products | Description |
| SSO and Federation Tools (e.g., Okta, Ping Identity, Microsoft Entra ID) | Provide centralized identity federation and SSO capabilities for seamless and secure authentication across AWS and other cloud applications. |
| MFA Tools (e.g., Duo Security, YubiKey, Microsoft Authenticator) | Enforce MFA for enhanced security, supporting push notifications, biometrics, hardware tokens, and password less options. |
| Passwordless Authentication Tools (e.g., Beyond Identity, Ping Identity, HYPR) | Enable secure, password-free authentication leveraging biometrics, device-based trust, and cryptographic techniques. |
Monitoring, Detection, and Response Recommendations: Securing Your Cloud Environment
Scope: Log storage, event and incident detection, and incident response for cloud security and governance.
Options for Configuration:
| AWS Native Tools | Description |
| AWS Console, CLI, API, or Infrastructure-as-Code (Terraform/ CloudFormation) | Utilize these tools to create Non-Human Identities (NHIs) and assign entitlements, ensuring consistency, scalability, and auditability. |
| External Products | Description |
| NHI Governance Tools (e.g., Natoma, Veza, Astrix) | Automate NHI lifecycle management, including creation, secure credential storage, and credential rotation, while enforcing Zero Trust principles. |
| IGA Tools (e.g., SailPoint, Saviynt) | Implement governance workflows for NHI entitlements, encompassing approval processes, periodic reviews, and compliance tracking, with integration for lifecycle management. |
| ITDR Tools (e.g., Microsoft Defender for Identity, CrowdStrike Falcon, SentinelOne Singularity Identity) | ITDR tools monitor and respond to identity-related threats by detecting compromised credentials, unauthorized access, and privilege escalations, thereby enhancing security posture. |
| NHITDR Tools (e.g., Entro, Astrix) | They specialize in detecting and responding to threats targeting NHIs by monitoring for abnormal behaviors, unauthorized interactions, and potential compromises, ensuring the security of machine identities. |
Decision Making
How to Create an IAM Strategy That Works for Your Business
Building a secure and efficient strategy for Non-Human Identity (NHI) governance, activity monitoring, and threat detection requires a comprehensive approach. These decisions can be complex, but with TechDemocracy’s proven Cloud Security Decision Framework—trusted by numerous Fortune 100 customers—you’ll make informed and tailored choices.
Factors to Consider:
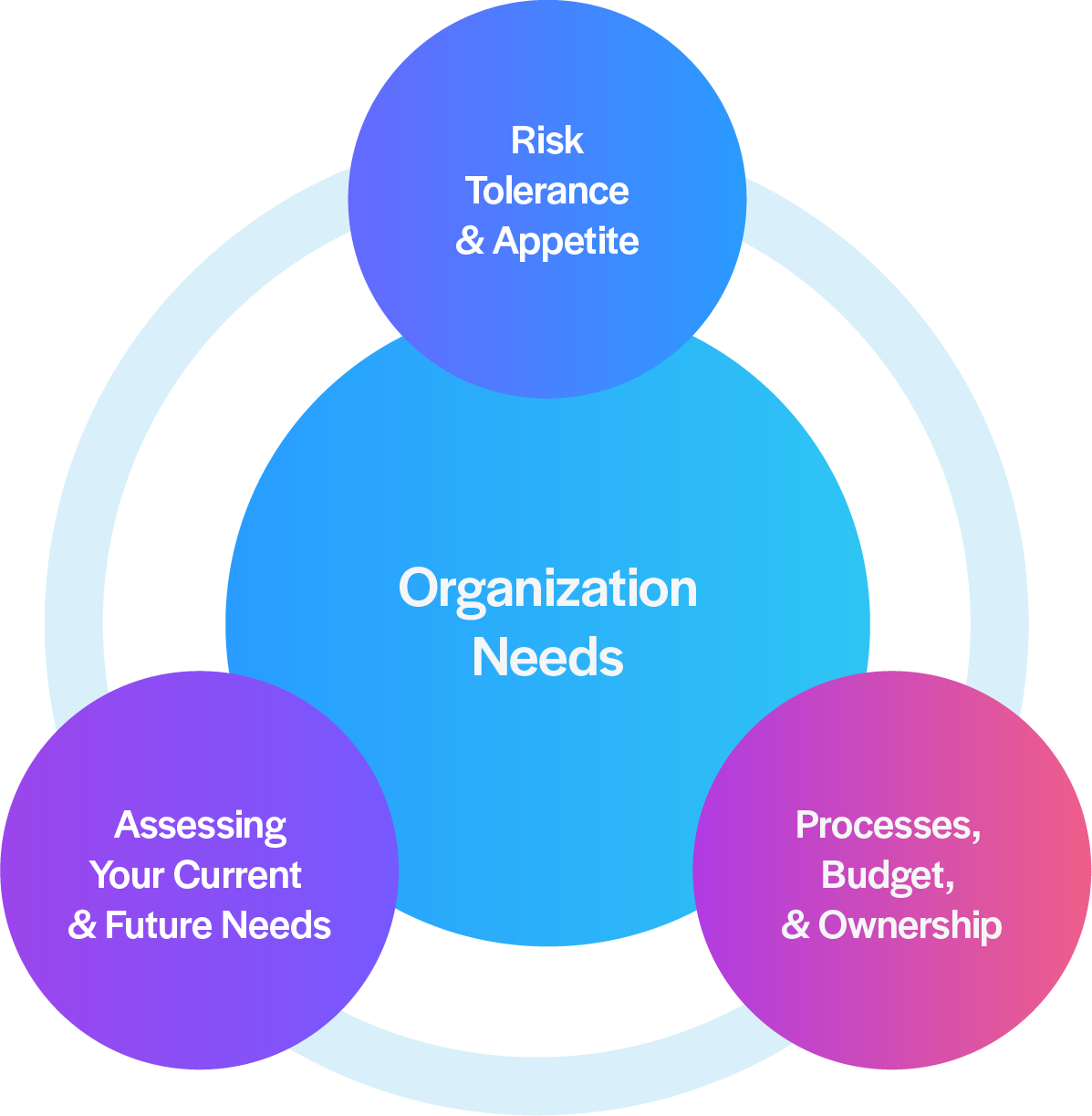
1. Risk, Compliance, and Security Context:
a. Risk Tolerance and Appetite:
Understand your organization's willingness to accept risks, ensuring the security strategy aligns with operational goals and acceptable risk levels.
b. Audit and Compliance Needs
Assess regulatory requirements for vulnerability management, change management, and monitoring to ensure adherence to industry standards.
Identify gaps in your current compliance efforts and plan for improvement.
c. Risk Classification of Cloud-Deployed Applications
Classify workloads based on sensitivity (e.g., critical, high-risk, or low risk) to prioritize security investments and monitoring efforts effectively.
2. Landscape and Roadmap for Tools:
a. Current Landscape for Cloud Security and Detect and Respond
Evaluate the tools currently deployed, such as CWAPP, CNAPP, CSPM, and other security platforms, based on the following factors:
Maturity: Assess how well the tools are integrated and utilized within your environment.
Skillsets: Evaluate the expertise available for managing, maintaining, and optimizing these tools.
Ownership and Responsibilities: Ensure clear accountability for the governance and upkeep of these tools.
Roadmap and Priorities: Review plans for tool upgrades, expansions, or replacements to ensure they evolve with your needs.
b. Current Detect and Response Tools
Evaluate your existing detection and response (DR) solutions, such as EDR, XDR, CDR, and SIEM tools, to assess their effectiveness and integration capabilities.
Identify areas for improvement to enhance detection and response through ITDR (Incident Threat Detection and Response) and NHITDR (Non-Human Identity Threat Detection and Response) solutions.
c. IDM Landscape:
Evaluate deployments of IGA, Privileged Access Management (PAM), Non-Human Identities (NHI), and Single Sign-On (SSO)/Multi-Factor Authentication (MFA) tools to ensure smooth integration and consistent governance throughout your identity and access management ecosystem.
d. Complexity and Effort in Data Synchronization and Integrations
Assess the level of effort needed to integrate AWS IAM with external tools like IGA, CNAPP, CSPM, and ITDR. Focus on identifying opportunities for automation to reduce manual processes, budget, and ownership to improve efficiency.
3. Processes, Budget, and Ownership:
a. DevOps Maturity
Evaluate the level of automation, scalability, and integration within your DevOps processes to determine the organization's readiness for implementing identity and security management solutions.
b. Organizational Structure and Responsibilities
Clarifying ownership, budgets, and accountability for the following areas is crucial:
Cloud Infrastructure: Who is responsible for managing infrastructure setup and operations?
Cloud Security: Who governs the tools and processes related to cloud security?
Security in DevOps: Who ensures the security of the CI/CD pipeline and secure deployment of workloads?
Cloud Security Tools Deployment: Who oversees the selection, deployment, and maintenance of security tools like CNAPP, CSPM, CWPP, and ITDR?
Conclusion: Building a Robust AWS IAM Strategy
Successfully implementing AWS IAM requires a strategic approach to managing policies, users, and non-human identities, while integrating external tools to boost security and compliance. Decisions should factor in elements like organizational risk tolerance, DevOps maturity, and the existing tool landscape.
Why TechDemocracy?
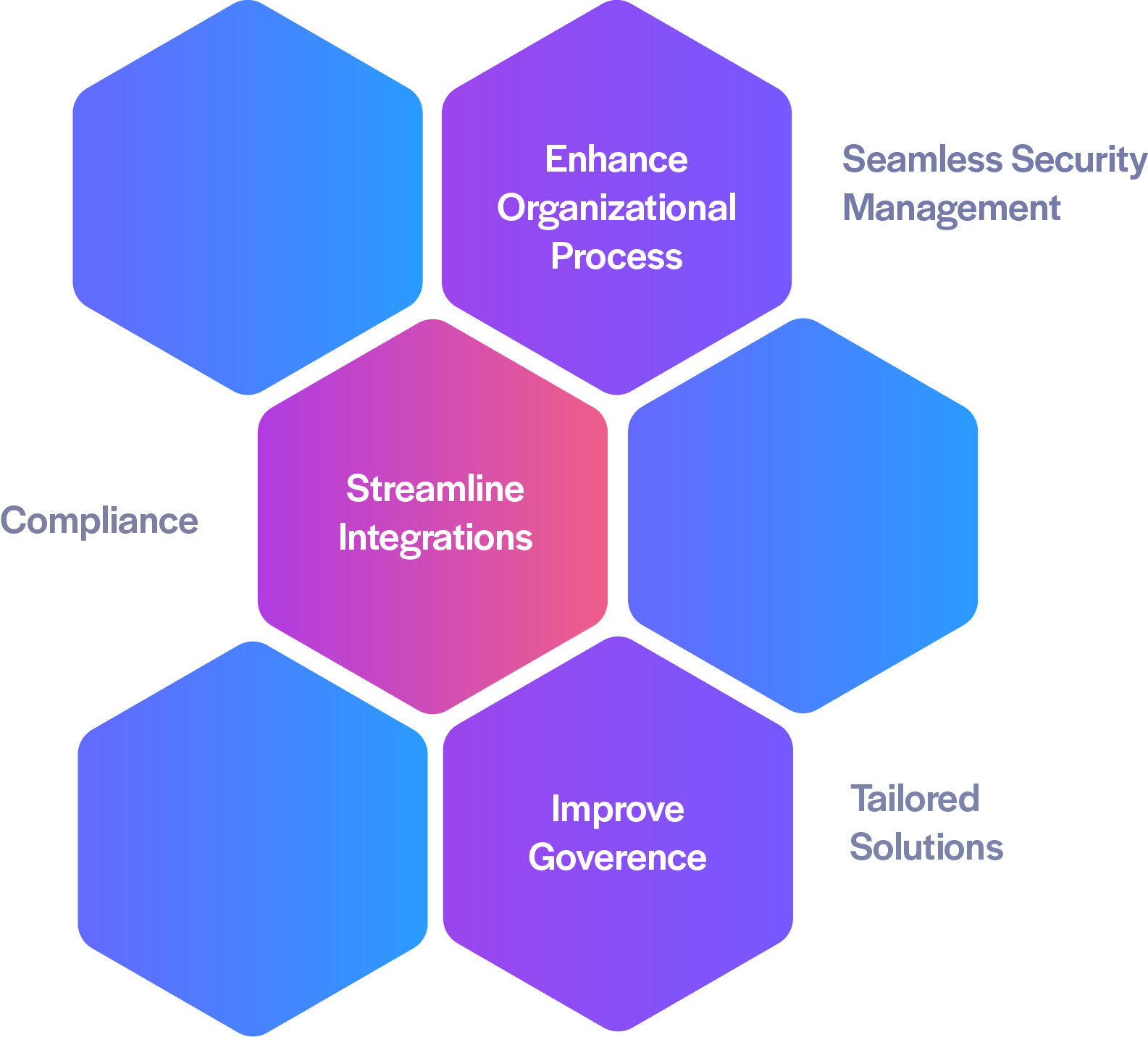
TechDemocracy specializes in designing and implementing secure, scalable cloud architectures tailored to your unique environment. By leveraging our Cloud Security Decision Framework, we:
- Align risk, compliance, and security goals with operational needs.
- Evaluate your tool landscape and roadmap for optimization.
- Streamline integrations, improve governance, and enhance organizational processes.
Contact TechDemocracy today to refresh your cloud security architecture, develop a comprehensive strategy, and implement innovative solutions for identity governance, cloud security, and threat detection. Let us help you establish a secure foundation for your cloud journey!
Recommended articles


Synthetic Identity Fraud: A Growing Threat to Enterprises
Take Your Identity Strategy
to the Next Level
Strengthen your organization's digital identity for a secure and worry-free tomorrow. Kickstart the journey with a complimentary consultation to explore personalized solutions.